Firewall Basics
We are now going to look at the basics of firewalls, at least enough for the very basic beginner. This will give you enough understanding to appreciate the finer points of Sygate P.F., but it is not a technical treatise, or an in depth discussion on the subject. If you are not a firewall beginner, or you just want to know more, I can recommend the website written by Jimmy Moore which you can access here , and which will tell you more than you need to know, and certainly more than my meager effort!
What Is The Internet?
The internet can be considered as one vast computer, with each PC as a node on each branch. When you are connected to the internet, you are connected to every other computer that is connected at the same time. Because of its original design to be a military communications system that could not be taken out in time of nuclear war, the various nodes have transmissions in packets of information, each packet of which might arrive by a different route, but once they come together, communication is made. Those packets of information leave from and arrive to a PC through PORTS on a PC.
What Is A Firewall?
A firewall is basically a filter for the packets of information that come in and go out of your computer. The filter is set up to obey certain rules that the user sets in order to make sure this traffic meets with the user's needs.
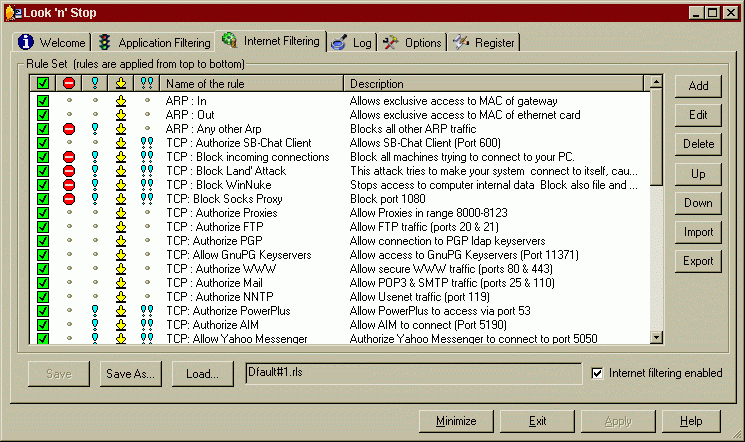
Rules based firewalls still use this basic system, as it is very flexible and you can get control over almost every aspect of how the filtering process works. Look'n'Stop is a modern rules based firewall of this type and to give you some idea of what its ruleset looks like here is a screenshot:

Although there is great flexibility with this kind of arrangement, it requires the user to know about the intricacies of rule generation and the like. That is where other firewalls, such as Sygate P.F. come in.
A new breed of firewalls, application based, have been around for a while. Using these, when an application is connecting to the internet you can decide which ports it will use; like wise, when a transmission comes in, if it wants to connect to an application, it is allowed to do so if you do not have a rule set to forbid it . This is different from the rules based programs where you deny or allow access to a port no matter which application is using it. In Look'n'Stop above, there is also application filtering, but only whether an application is allowed or denied. As you can appreciate to be able to set rules per application is easier, but does not cater for the situation where an application has not yet connected to the internet but you never want it to.
To a certain extent, some firewalls have overcome this by having an Intrusion Detection System (I.D.S.). This can be thought of a set of rules which are hard coded into the firewall. None that I have come across is as good or extensive as that in Sygate P.F., with the possible exception of Back Ice Defender (B.I.D.) which is a separate program that was originally devised to accompany such programs as Zone Alarm. But B.I.D. does not adequately filter outgoing connections and therefore does not perform in the same way as the Sygate P.F. I.D.S. and from testing I have done, I would say it is not as good.
Sygate P.F. has extensive Application Rules, but it really comes into its own with the Advanced Rules. Though these are global (ie. not tied to a particular application) you can deny access to applications on a port basis BEFORE you have the application connecting. There is a whole section on the Advanced Rules, for more information, click on the button at the top of this page.
wilders.org Description Of How Firewalls Work
A good analogy of HOW a firewall works can be found at wilders.org , likening the flow of transmissions in and out of your computer much like the telephone exchange in a large hotel. Part of it is reproduced below, by permission.
These terms can be easily understood by analogy. If you are familiar with telephone systems, think of the Internet as compared t the world-wide telephone network. Here are the analogies for the other terms:
computer system: a hotel with phones for staff and guests
TCP/IP: a person-to-person call
UDP: voice mail (leaving a message)
Port: a telephone extension number
Address: the telephone number of the hotel
Connection: a telephone call
Firewall: the hotel telephone operator
ARP: finding a street address
The hotel telephone system is analogous because the PC plays host to the applications you run. Setting up a firewall will be like telling the hotel operator how s/he is allowed to let calls and messages get through. You, the computer user, are both "hotel manager" and "VIP Guest".
concept 1:applications and services
Hotels have guests and hire staff that serve guests.
FIREWALL: computers have applications (e.g. email, web browsers)
and use operating services (e.g. DNS, RIP, Identification) to support these
applications.
concept 2:communication
A person in the hotel wants to phone out. He is calling frome a phone with an extension number to
another person in a different hotel, also with
a phone and extension number.
FIREWALL: an application or service in your PC wants to
communicate with another application or service on another system.
With TCP/IP and UDP/IP, communication uses IP addresses of the
computers and port numbers.
concept 3:without a firewall
Without an operator, anyone may call in or out. There may be nobody at
that extension. Alternately, the person may or may not answer their phone.
FIREWALL: without a firewall, communications are freely attempted, in
or out. Not all ports have services using them. Alternately, an
application/service may or may not accept a connection attempt.
concept 4:role of a firewall
When the operator is working s/he decides which extensions may make
calls and which other hotel and extension they may call.
FIREWALL: when the firewall is running, it decides what systems may
communicate and what port numbers may be used.
concept 5:blocking incoming TCP/IP connections
An operator can block an incoming telephone call to a person while
allowing that person to make outgoing calls.
FIREWALL: a firewall can block incoming connection attempts on any
particular TCP/IP port while allowing the same port to be used for
outgoing connections.
concept 6:this firewall is a "packet filter"
The operator can block a call, but does not censor what is said. A security chaperone might help.
firewall: a (packet filter) firewall can block communication but does not inspect the contents of the
data packets. Anti-virus software might help.
concept 7:TCP/IP compared to UDP/IP
Some people always make "person-to-person" calls and others leave a
message. When you leave a message you are never quite sure that the
other person got it.
FIREWALL: applications either use TCP/IP to make a connection or
they use UDP/IP to send a single "datagram". With UDP/IP, you are
never quite sure the other application got it.
concept 8:blocking UDP/IP data
If the operator is instructed to allow a guest to leave messages for another
person in another hotel, then s/he will also allow that other person to
leave a message for the guest.
FIREWALL: if the firewall has a rule to allow applications/services to
send UDP/IP to another system(s) on certain ports, that other system(s)
may send to you using the same ports. The reason is that it's not clear
when the system is replying to you and when it's taking the initiative.
concept 9:how ports are used
The white courtesy phone in the lobby is available for all guests to make
outgoing calls. Typically, hotel staff can be reached at extensions 1 to
1023. Courtesy phones have extensions 1024 to 5000. This way, guests
don't tie up extensions assigned to hotel services (room, service, front
desk).
FIREWALL: a range of (local) ports is available for applications that
communicate with services on other systems. Typically, services are
available on ports 1 to 1023. Ports for temporary use range from 1024
to 5000. This way, applications/services don't tie up a port assigned to
your systems services (file shares, identification etc.).
concept 10:how ports are used (2)
A convention in the hotel business is that the lounge is at ext. 80, the
concierge is at ext. 53, a bellman is at ext. 23 etc. This way, guests know
how to reach staff in other hotels. Guests are kindly requested not to use
the staff's extensions for personal calls.
FIREWALL: a convention in the TCP/IP and UDP/IP protocols in that
particular services are available at particular ports, e.g. web servers are
at port 80, DNS at 53, telnet at 23, etc. This way, your applications know
how to reach services on other systems. Applications should not use these
extensions inappropriately.
concept 11:rule usage
This hotel has an operator that can be instructed to allow certain calls
through under certain circumstances, such as 1) only when a certain
guest is in the hotel 2) when cell phones are in use 3) when a call is going
through the hotel's secure phone lines etc.
FIREWALL:with a firewall you can make a rule that allows certain
communications only under certain circumstances, such as:
1) when a certain application is running
2) when dail-up connection is alive.
concept 12:priority of rules
Some instructions for the operator are more important than others. By
assigning a priority to each one, one controls the order in which the
operator reads and applies instructions.
FIREWALL: some rules take precedence over others. By setting the
priority you can control the order in which rules are used and applied.
I hope that this helps you to understand the nature of firewalls in a more illustrative manner. And these are some of the dangers that exist on the internet for which you would be well advised to get a good firewall, like Sygate P.F.:
IRC and chat nuking
People who use chat groups (IRC, ICQ) tend to invite harassing interference from other malicious chatters. These lamers send "ICMP nukes" and other datagrams to tell your system that it can no longer reach the chat server. A firewall can block this.
Eaves Dropping
Even though your system is communicating with another computer, it is travelling on a shared network so other computers can acces the information that is sent.
Authentication
Computers can alter their IP addresses and pretend to be another trusted system and fool the firewall. It is up to applications to authenticate the remote system, use a secure connection.
TCP connection hijacking
It's possible for a hacker to intercept a TCP connection you have, tell the other system the connection is closed, then pretend to be them. Without a secure connection made through a firewall your system would never know.
DNS spoofing
If a hacker can interfere with DNS (Domain Name Service), they can supply you with an incorrect IP address and make your system talk to the wrong computers.
Altering of Data
If a hacker can intercept your communication, they can alter data. A secure connection provided by a firewall solves this problem.
A firewall does not do investigation and cleaning of your system; it can only make the transmissions by a virus or a trojan horse impossible to get in or out.
What Are Protocols?
There are basically three protocols that you will encounter in using firewalls: TCP, UDP, and ICMP. Here is a very basic introduction to them, for a more extensive explanation see Daryl's TCP/IP Primer.
TCP is part of the basic protocol whic h controls the internet, TCP/IP. It controls the flow of data between two ports in which if the packet data is dropped, it is resent. It is used in both Sygate's Application Rules and Advanced Rules, and will be the main protocol you will set.
UDP is basically the same as TCP except that it if a data packet is dropped, it is not resent. It is used in both Sygate's Application Rules and Advanced Rules, and is typically used in game server connections.
ICMP is used for out-of-band messages related to network operation or mis-operation, such as announcing network errors, announcing network congestion, pinging, and assisting troubleshooting. It can also announce timeouts in transmissions. This is found only in Sygate's Advanced Rules.
By knowing which protocol you are limiting by the Rules you set, you can acheive different effects. A good way to know which protocol you need to use in Sygate P.F. is to use the Traffic Log. We shall be coming to this in a later page.
In Summary
SygateŽ is a registered trademark of Sygate Technologies, Inc